By: Trevor Howe, Senior Operational Resilience Consultant
On September 26th, sudden drops in pressure were observed in the natural gas pipeline Nord Stream 2 before undersea leaks were detected in the Baltic Sea. Shortly thereafter, leaks were also detected for Nord Stream 1. While the pipelines are not currently facilitating gas flows from Russia to Europe, they were filled with natural gas which has leaked into the Baltic, creating an operational hazard for vessels in the area. The Prime Minister of Sweden, Magdalena Andersson, disclosed to a news conference on September 27th that seismologists in Sweden, as well as Denmark, had registered two powerful blasts the day prior in the vicinity of the leaks. Moreover, the explosions occurred in the water, not under the seabed, and at relatively shallow depths which would be reachable by divers or unmanned underwater vehicles.
Nord Stream Sabotage Damages European Energy Infrastructure
While these explosions occurred inside the exclusive economic zones of Sweden and Denmark, they have not been considered an attack on either country, which could trigger NATO intervention through Article V of the Washington Treaty. European Officials, including NATO, have claimed that the explosions were the result of sabotage, though the European Union has not yet named a perpetrator or suggested a reason behind the incidents. The Kremlin’s spokesman, Dmitry Peskov, also told reports that the incidents could have been the result of sabotage and that they would promptly investigate the matter.
While investigations are underway to ascertain the cause of the explosions and responsible parties, neither pipeline was active and these incidents should have no immediate effect on the supply of natural gas to Europe, though they have put additional upward pressure on prices.
Operational Threats Against Energy Infrastructure & Supply Chain
What the Nord Stream events highlight is the fact that European critical infrastructure can be a potential target for those seeking to precipitate disruptions and undermine energy security on the continent. This threat is made particularly dangerous amid EU Member States’ efforts to prepare for the winter season without Russian natural gas.
The speaker of Lithuania’s parliament, Viktoria Čmilytė-Nielsen pointed out that “these incidents show that energy infrastructure is not safe” and that “[the explosions] can be interpreted as a warning.” If indeed these explosions were intended as a warning, it is possible the threat could be directed towards the Baltic Pipe, a new gas pipeline carrying supplies from Norway through Denmark to Poland which was just opened on September 27. Norway has been a crucial supplier to Europe amid the scramble to replace Russian energy, so disruptions to Norwegian exports could have significant downstream effects. However, it is crucial to note that this threat is not unique to Norwegian energy infrastructure.
Cyber Threats Against Energy Infrastructure
While physical threats to critical infrastructure (as defined by Council Directive 2008/114/EC of 8 December 2008) are a priority for EU Member States, governments must also prepare against cyber threats. According to the Commission, “traditional energy technologies are becoming progressively more connected to modern, digital technologies and networks,” and while this makes the energy system smarter, “digitalization creates significant risks as an increased exposure to cyberattacks and cybersecurity incidents potentially jeopardizes the security of energy supply and the privacy of consumer data.”
One need only look to the disruptions caused in the U.S. in the wake of the ransomware attack against the Colonial Pipeline Company in May 2021 which led to the shutdown of 5,500 miles of pipeline carrying around 45% of fuel supplies on the East Coast. That attack was made possible by a single password being compromised for a legacy virtual private network (VPN) which didn’t use two-factor authentication. A relatively simple theft enabled hackers to disrupt one of the country’s largest and most vital pipelines, forcing President Biden to declare a state of emergency.
Europe is not immune to threats similar to the Colonial Pipeline cyberattack. Early February 2022 saw a slew of cyberattacks against oil transport and storage companies across the continent. These attacks forced an affected company, Oiltanking Deutschalnd GmbH & Co. KG, to operate at a limited capacity and even caused slowdowns at ports in the Netherlands as barges awaited oil deliveries. With supply chains in a state of recovery due to the COVID-19 pandemic, disruption events like this have the potential to set recovery efforts back significantly, especially at a time when energy security in Europe is a top priority.
Russian Hybrid Warfare
Though Russia has wielded energy as a foreign policy weapon, by cutting flows entirely through the Yamal pipeline and Nord Stream 1 the Kremlin has lost leverage in terms of the future damage it can unilaterally instill via energy exports to Europe. As a result, it would be unsurprising if Russia were to employ additional hybrid warfare tactics in the form of cyberattacks, an area in which the Kremlin wields asymmetrically advanced capabilities, to further Russian national interests. These could include attacks which target critical energy infrastructure to further destabilize Europe’s energy security and put more upward pressure on energy prices which threaten business’ operations across the continent.
Multiple entities in Russia are known to possess and deploy advanced cyber capabilities against adversarial targets, this includes Russia’s Federal Security Service (FSB); Russia’s Military Intelligence Agency (GRU); Russia’s Foreign Intelligence Service (SVR); and a private organization, the Internet Research Agency (IRA). These actors can act alone, or in tandem with one another, to devastating effect if they so desired to further destabilize Europe’s energy security.
Supply Chain Risk Management
To guard against physical disruptions, Norway and Denmark have already stepped-up security posturing around their oil and gas industries’ infrastructure, rigs, and buildings after the Nord Stream incidents. However, physical security does not guard against cyberattacks which can be mounted from halfway across the world.
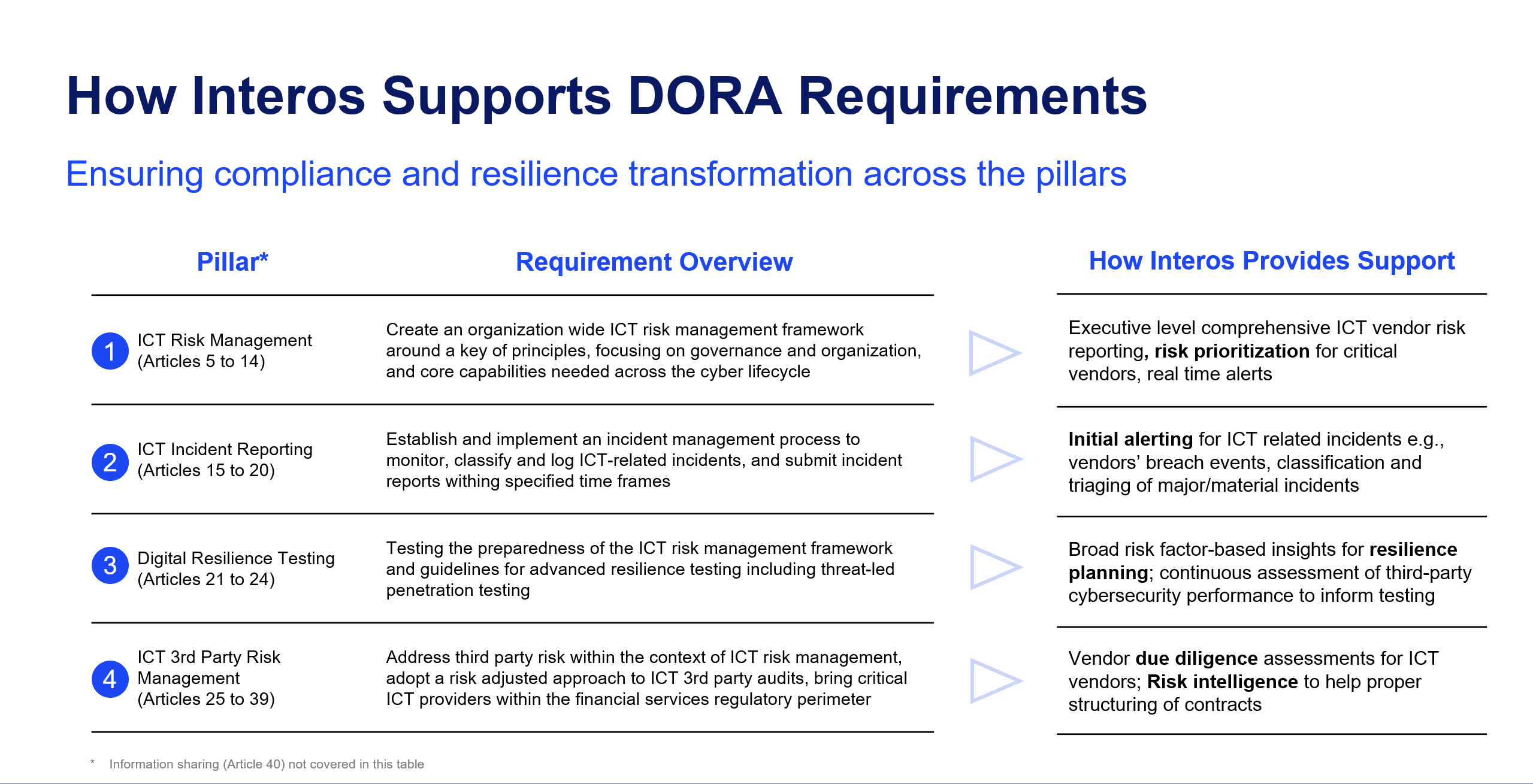
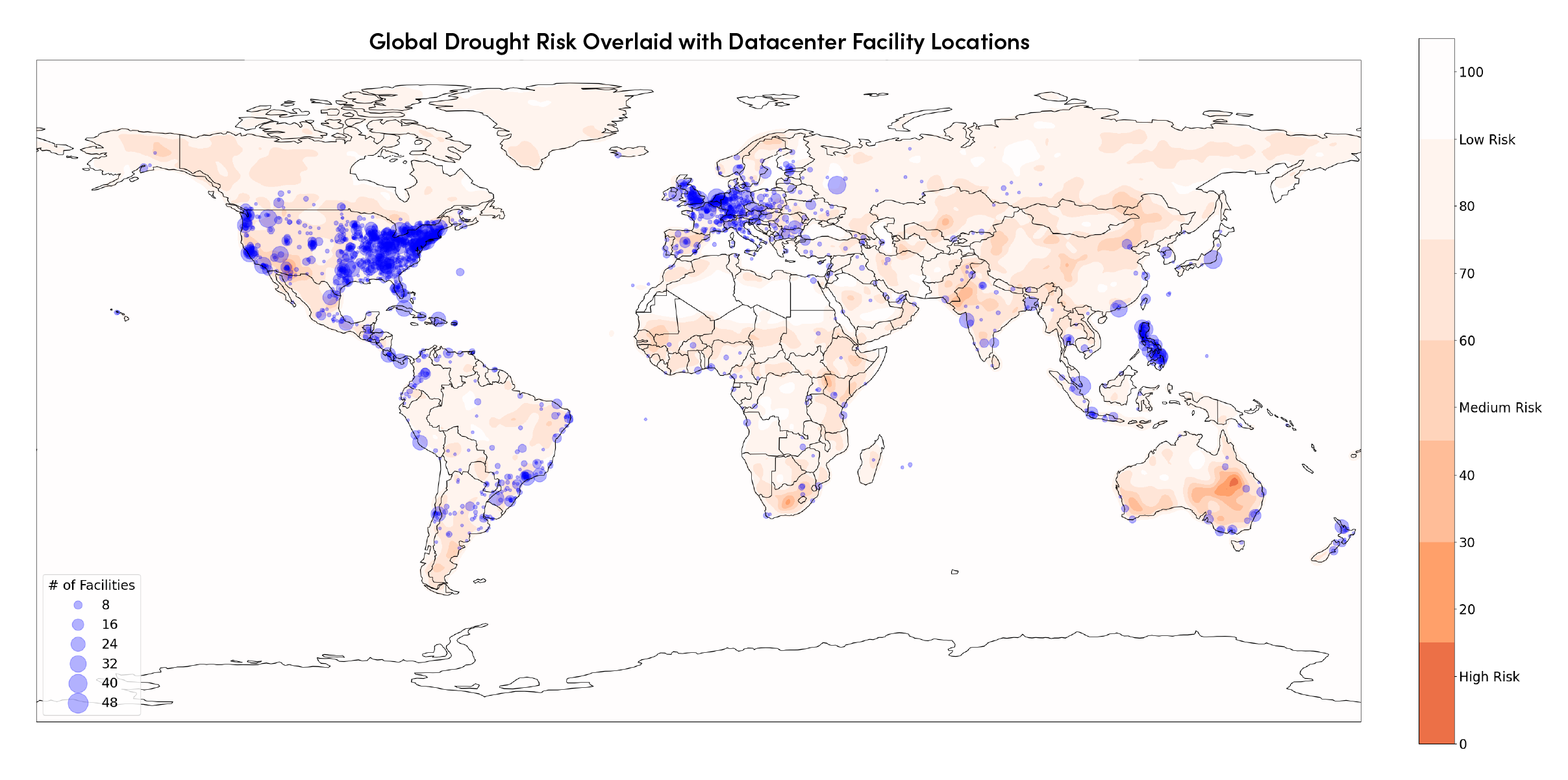
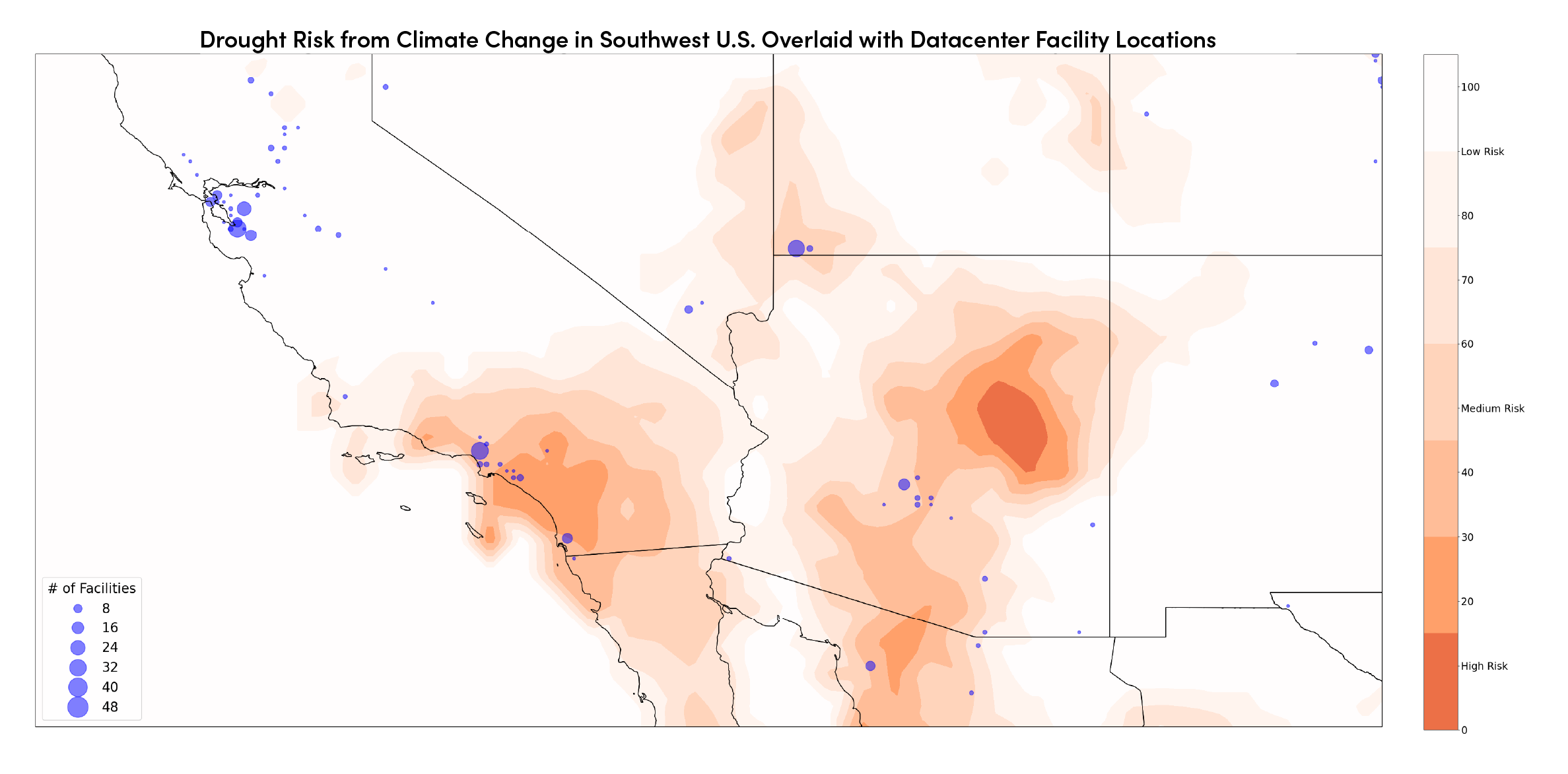
Companies can better-understand their risk exposure to physical and digital infrastructure attacks by gaining greater visibility into their third parties’ risk posture. Doing this at-speed, continuously, and without breaking the budget requires artificial intelligence-driven software like the Resilience platform offered by Interos.
Additionally, entities should implement risk management programs, conduct internal reviews to assess their own security posture, prepare and test resilience plans for likely scenarios, and strengthen collaboration with stakeholders in their respective industries to better manage risk in their supply chains.