By Interos Labs (Andrea Little Limbago & Joshua Clarke)
This week’s disclosure of a Russian firm masquerading as an American company highlights yet again the potential security concerns hidden within software supply chains.
The company, Pushwoosh, provides coding language and data processing for companies building software applications. Its code allows software developers to track and profile app users to customize the notifications they receive.
While Reuters’ exclusive story noted Pushwoosh’s integration with the Centers for Disease Control and Prevention (CDC), that agency was far from alone. Interos’ own analysis has identified additional industries and countries most at-risk of exposure to Pushwoosh code and potential data breaches.
We have also noted some of the tell-tale signs that organizations need to be on alert for regarding company ownership and location.
Pushwoosh and the Digital Supply Chain
At a time of growing concern over the national security threats within the information and telecommunications (ITC) supply chain, the Pushwoosh revelations are yet another reminder of the challenges and complexity of modern digital supply chains. Following on from last year’s investigations into JetBrains, a software company founded by three Russian engineers based in the Czech Republic, the Pushwoosh revelations have sparked similar concerns over foreign ownership risks.
They are also the latest reminder of the challenges and complexity of modern digital supply chains.
Pushwoosh is integrated with thousands of applications in major app stores and includes tracking software that allows Pushwoosh to collect sensitive Personally Identifiable Information (PII).
Depending on the application, the PII includes precise geolocation and health history information, “which could allow for invasive tracking at scale”, according to an expert quoted in the Reuters story.
Pushwoosh claims to be a Maryland-based company, but Russian filings list it in Novosibirsk, Russia. Instead of revealing its Russian location, Pushwoosh has previously listed under California and Washington, D.C. area addresses.
This deception not only masked the foreign ownership risk, but — considering Russian data collection policies — also put customer data at risk of seizure by Russian security services.
Hiding in Plain Sight?
Based on our analysis of Pushwoosh’s presence within global supply chains, we identified the top 10 industries and countries affected (see table).
Top 10 Industries and Countries for Pushwoosh Customers
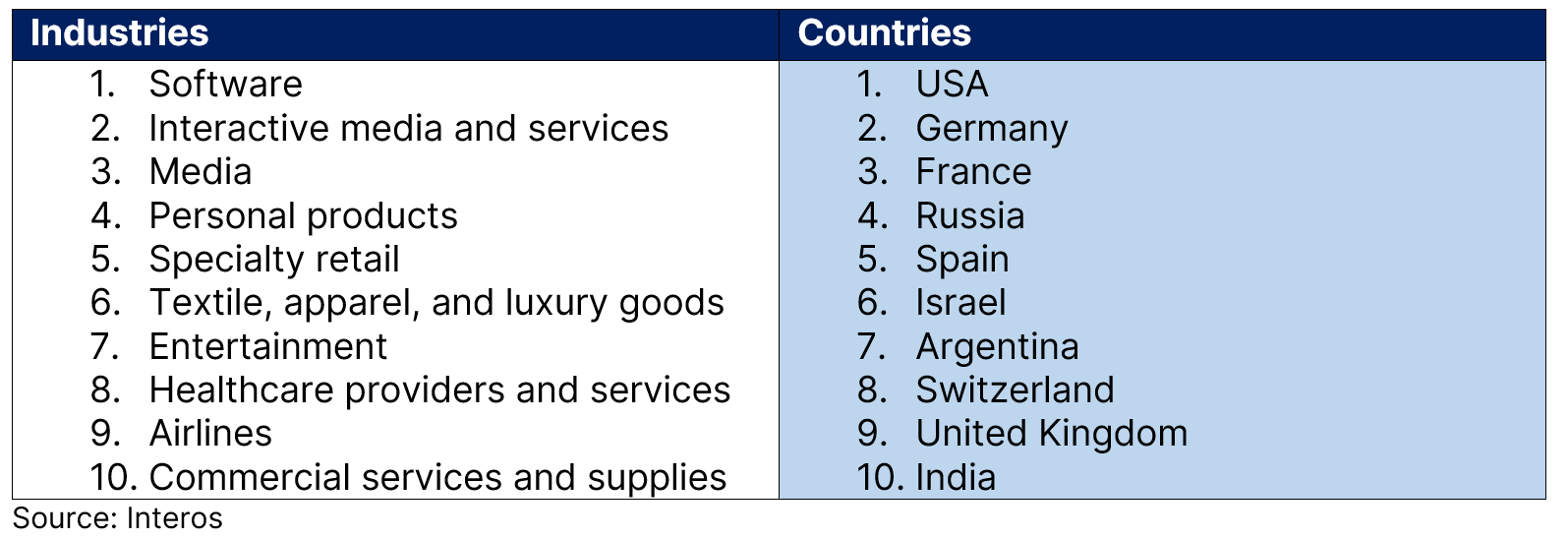
While US software firms had the greatest single country-industry exposure, the prevalence may be much more limited in comparison to other supply chain vulnerabilities, such as Log4J.
Nevertheless, among those identified are several European industrial firms, a major US publisher, a cybersecurity company and Ukrainian telecom and transportation providers.
Pushwoosh has a breadth of Russian connections, including relationships with the following entities, some of which are on US restrictions and prohibitions lists:
- TNT (Russian TV station, parent company Gazprom)
- Ozon (aka the “Amazon of Russia”)
- Rambler Media
- Yandex
- Mail.ru Group Limited
Pushwoosh’s significant footprint and integration across restricted and/or highly influential Russian companies should have been an early indicator of risk that warranted additional investigation of foreign influence.
Moreover, when looking into a range of open-source activity, it becomes clear that major Pushwoosh contributors have strong Russian connections or are Russian themselves. This underlines the growing importance of the Software Bill of Materials (SBOM), which not only is a security risk but will be a compliance risk as federal regulations continue to address SBOM requirements.
Gaining Visibility Across Your Supply Chain
This latest example of digital supply chain vulnerability comes on the back of a year of high-profile discoveries. Pushwoosh reflects the digital supply chain risks that can emerge from untrusted technologies within a company’s ecosystem.
Importantly, this is a case of a vendor deemed trustworthy, and so it remained off the radar until the recent exposure. The movement toward trusted networks was already well underway; Pushwoosh will likely reinforce the message that additional due diligence of ICT vendors is necessary.
At Interos, we provide the visibility into your extended supply chain, including identifying sanctioned foreign companies and their supply chain partnerships. We recommend reviewing your own extended supply chain to confirm whether Pushwoosh is present. Very often untrusted vendors are not in the first tier but rather are hidden in the second tier, third tier,
If you are concerned about the presence of Pushwoosh in your digital supply chain – or want to increase the resilience and visibility of your entire supply chain – contact Interos here.



